Outbreak, Armageddon, 2012 and Hollywood’s list of “save the world” movies goes on! It seems that Hollywood has been preparing humanity for a disaster for years now (2020 is the 25th anniversary of Outbreak) and none of the plots seem as far-fetched now. As New Year 2020 approached, no one could have fathomed that the world in 2020 would essentially come to a complete halt! However, a silver lining in this story is the design of our electronic systems and the robust design of the Internet. This has been the backbone and the digital enabler of keeping the world moving during these times.
As the global economy shrinks into recession and world leaders explore ways of revival, enterprises are re-evaluating current spends and working on optimising these through digital transformations. The raison d’être for Digital Transformation can be summed up as optimising the per unit transaction cost . This is not difficult to comprehend for those with an economics background, where savings after meeting variable costs contributes to offsetting the fixed costs for the enterprise. In pure business terms, one can consider this as efforts to improve gross profit or gross margin.
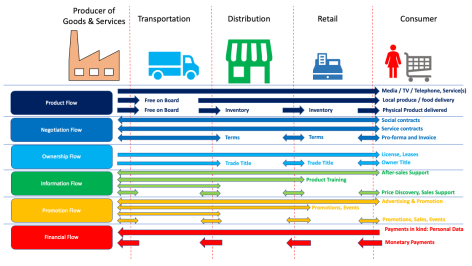
Conceptually, the target areas for Digital Transformation are those which lie in the path of a transaction. Accelerating digital transformations across business flows in any transaction can potentially help optimise business, reduce spend and shorten the quote-to-cash cycle. These business flows typically are:
- Product Flow: This is the physical movement of good and services from producer to consumer, involving intermediaries
- Negotiation Flow: Comprises of the negotiation between producer, intermediaries and consumer to “strike the deal”
- Ownership Flow: This is the transfer of title, which can be as simple as making payment against an invoice or as complex as registering a vehicle or house
- Information Flow: Consists of information exchange between all parties pertinent to the transaction – product details, sales support, pricing etc.
- Promotion Flow: Persuasive communication targetted at the intermediaries or to the consumer
- Financial Flow: The payment to the producer, in cash or kind, for the product or services provided
These flows are generic and this analysis can be applied to enterprise, non-profit and government. However, not all flows can be digitally transformed for all businesses. For example, in certain services, like hair-dressers, masseurs, physio-therapists, unless robots take over the job, the product flow may not be ready for transformation.
So where and how does an organization digitally transform its transactions? The approach is to automate what is currently done through a manual process, shorten processes, reduce toil (repetitive work), and accelerate innovation. In simple terms, take what you have and find ways to make it “better, faster, cheaper”!!! While, there is no “one size fits all” blueprint, technology adaptation across these flows has the potential to disrupt and/or transform. The key enabling technologies for transformation in this decade are:
- Big Data and Advanced Analytics
- Artificial Intelligence and Machine Learning
- Mobile technologies
- Virtual / Augmented Reality
- 3D Printing
- Chatbots and Virtual Assistants
- Internet of Things
- Blockchain
- Robotics
A map view of these technologies in their applicable flows are depicted below.
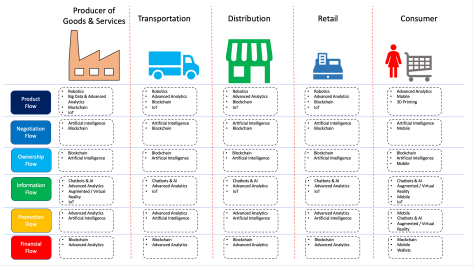
Big Data and Advanced Analytics
With a large amount of data collected through Enterprise Resource Planning (ERP), Contact centers and e-Commerce storefronts, Big Data and Advanced Analytics are being used to provide actionable insights into the consumer buying behaviour, product design and optimisations in delivery and retail. The models being built, tested and used by big businesses will eventually be productised for medium and small businesses to adopt.
Artificial Intelligence and Machine Learning
In conjunction with other technologies, Artificial Intelligence and Machine Learning models are being developed. These have the capability to power a variety of tools that can be used across the different flows. For example, a tool to help a salesperson determine the interest level of a prospect and provide the right incentive to help close a transaction faster (negotiation flow) or another using computer vision to evaluate proof of purchase (and ownership) to determine service entitlements (information flow).
Mobile Technologies
Mobile technologies has been at the forefront of all Digital Transformation stories. The global adoption of mobile is well understood. The transformation in this field has largely been through the deployment of Apps for individual brands and businesses. However, the next wave is also well in progress. The now forgotten BlackBerry mobile from Research In Motion (Blackberry Inc) was used in Indonesia for transacting a huge number of local services. A similar model is followed by WeChat in China and KakaoTalk in South Korea. The recent Facebook tie up with Reliance Jio for promoting Whatsapp in India is another example of this strategy being implemented. Incorporating such models and including a larger population will drive the benefits of the network effect, and trigger a virtuous cycle.
Virtual / Augmented Reality
Video and computer games are familiar to all of us and with a world in lockdown, video conferencing has become a new normal. Here in Singapore, the phase 1 easing has allowed realtors to show tenants and buyers, property, through virtual means. As social distancing becomes the norm globally, Virtual / Augmented reality solutions will be used along with other technologies – mobile, video games (for example Second Life). Musical concerts have been performed in the past using holograms and perhaps a number of service industries – entertainment, education, realty, heavy engineering (Product flow) will digitally transform using these technologies.
3D Printing
3D printing has come some way and today can print using different materials – plastics, metals and even wood. With the world changing its consumption habits to a do-it-yourself (DIY) model, manufacturing of products or their components may well be within the consumers’ own homes or in a larger scale neighbourhood “3D builder” farm. Ikea (Global), PepperFry (India), HarveyNorman (Asia) may offer 3D diagrams and the user construct the parts at or near home and DIY assemble it. This impacts product flow shifting the manufacturing away from a central location, removing the need for long distance transportation and changing the information flow.
Chatbots and Virtual Assistants
As more transactions move online, the opportunity for a salesperson to provide information reduces. Chatbots integrated with web-sites and with the mobile strategy provide an opportunity to integrate into the information flow and help provide necessary details and incentives to convert the view. Chatbots and Virtual Assistants have been around for a few years now and they are getting smarter by leveraging other technologies like Artificial Intelligence, Advanced Analytics and Mobile.
Internet of Things
The Internet of Things is as vast, if not larger, than the Internet itself. It has the promise to encompass every device owned by every person and more. IoT can generate and consume much of the information within its own realm. A popular example is the refrigerator communicating to the owner about the lack of milk and building out a shopping list. I personally would like my coffee machine to order the grinds and capsules. Other aspects of IoT would be to monitor performance of home appliances and order replacements and repairs (Information flow). Yet other aspects of IoT would include the ability to determine the condition of products from farm to fridge and reduce wastage.
Blockchain
Blockchain’s popularity soared with BitCoin and other digital coins. As it has matured, Blockchain is expanding to provide immutable, secure and open transactions in the business world. It has been adopted in supply chains. Going forward, adoption of Blockchain in the consumer side of business can drive improvements in the product, negotiation, ownership and payment flows. Blockchain could hold every component of every product sold to a consumer and this information can be used effectively for speedier up-sell / upgrades, recalls and replacements. The negotiation and ownership flows can be transformed through the use of smart contracts which execute the terms of the trade. Payment flows can also rely on these smart contracts.
Robotics
Finally robotics is another large topic. Robots have many different shapes and forms. They can be wheeled, legged or flying (drone). Today this is an experimental field, and it is a matter of time before they become mainstream. Their purpose can range from warehouse robots, manufacturing robots, service robots and even last mile delivery robots. Our daily consumption of grocery, food, medicines come from supermarkets and restaurants near to our places of residence or work. If product manufacturing were to move to neighbourhood builder farms (see 3D Printing above), this would add to the list of delivery requirements for robots to fulfil.
These technologies are not the only ones, and enterprises across the world are at different stages of digitalisation. Some are in early stages of their journey and are adopting common-of-the-shelf (COTS) systems while moving away from in-house application for their basic systems of engagements and of record. Others are at advanced implementations and adapting these. The common disruptor in all of this is of Cloud Computing, which is providing the new entrants the ability to leapfrog into the next generation of solutions.
Digital transformation also implies a potential to change business models. Any conversation on the topic is this incomplete without at least a mention on new business models. Digitalisation of the business flows, are transformative. However, startups have always charted their own ways to define disruptive models favouring exponential growth. Some or all of these models could be applied at various stages of the flows and/or technology strategies presented. These models include (and are probably the topic of a later blog):
- The Crowd Economy: Leverage crowd sourcing and crowd funding and receive “stuff” on demand
- The free / data driven economy: Platform driven bait and hook or provide free access to a cool service (ie. Facebook), provide your personal details and receive goods and services
- The Smartness economy: Add Artificial Intelligence (AI) to old world tools
- Closed loop economies: Offer waste free systems covering cradle-to-cradle services
- Decentralised Autonomous Organisations (DAOs): Organisations with no employees or management and non-stop production
- Multi-world models: Business model revolving around delivering services through Augmented reality or Virtual reality
- Transformation Economy: Pay to have your life transformed by the experience. Starbucks provides you a “third place” which is not office and not home and facilitates creativity and productivity.
In this blog, I have attempted to provide a perspective on Digital Transformation. It is must also be stated that this transformation will not occur overnight. For the transformation to be successful, it will also need to be inclusive and connect those members of society, who are not current participants in the digital era. As enterprises adopt some or all of these, I expect it will take us through this decade of the “20’s”.
 We collected our components in right earnest and went to the market to buy stuff we didn’t have. Here’s what we ended up with – Arduino, Raspberry Pi, USB WiFi dongle, relay board for Arduino, several meters of Reverse Osmosis (RO) water pipes, solenoid valve, power supply, manual valve for water supply connection. We also needed to use several solutions on the Cloud and Internet – an IBM Cloud and a Dynamic DNS account.
We collected our components in right earnest and went to the market to buy stuff we didn’t have. Here’s what we ended up with – Arduino, Raspberry Pi, USB WiFi dongle, relay board for Arduino, several meters of Reverse Osmosis (RO) water pipes, solenoid valve, power supply, manual valve for water supply connection. We also needed to use several solutions on the Cloud and Internet – an IBM Cloud and a Dynamic DNS account. The solution was simple – the plants were lined up in two of our balconies in rows and the RO water pipes were stretched across them. At each plant, a tiny hole was drilled into the water pipe, adjusting the size of the hole to ensure adequate pressure was available till the last plant in the row. The pipes were connected to the apartment plumbing through an electrically operated (solenoid) valve. The valve was connected to the control equipment built using Arduino and Raspberry PI.
The solution was simple – the plants were lined up in two of our balconies in rows and the RO water pipes were stretched across them. At each plant, a tiny hole was drilled into the water pipe, adjusting the size of the hole to ensure adequate pressure was available till the last plant in the row. The pipes were connected to the apartment plumbing through an electrically operated (solenoid) valve. The valve was connected to the control equipment built using Arduino and Raspberry PI. 



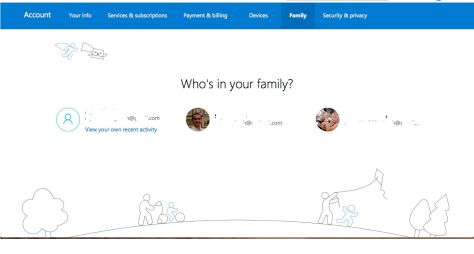
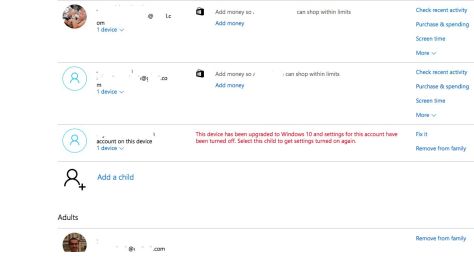
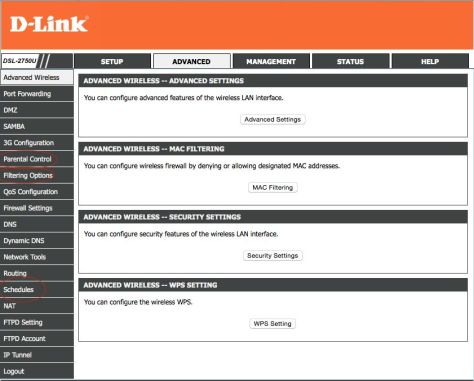
 The option to turn on Restrictions is under “Settings” and “General”. The screen shots show the options on an iPad and on an iPhone / iPod Touch.
The option to turn on Restrictions is under “Settings” and “General”. The screen shots show the options on an iPad and on an iPhone / iPod Touch.


 The “Camera” option is left on as this allows the children to use the camera on the device. Switch it off if you don’t want them to take pictures.
The “Camera” option is left on as this allows the children to use the camera on the device. Switch it off if you don’t want them to take pictures.


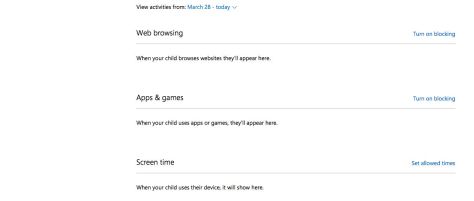
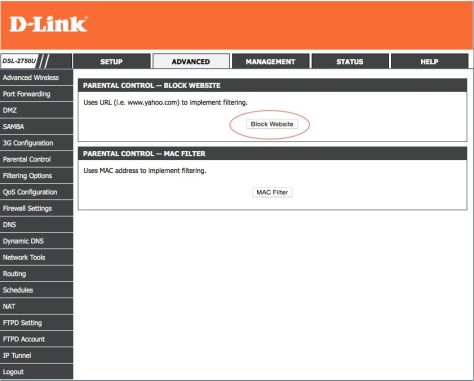
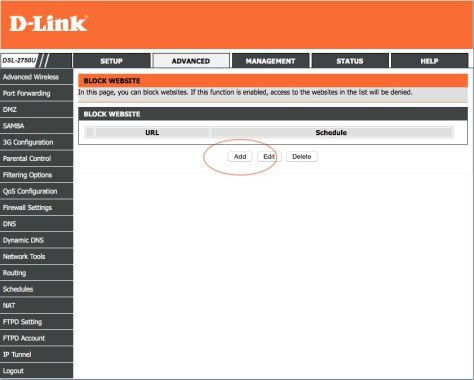
 To enable restrictions on the content they have access to, you’ll need to select “Ratings For” and select the geography (in this case India) for which you want to enable the settings.
To enable restrictions on the content they have access to, you’ll need to select “Ratings For” and select the geography (in this case India) for which you want to enable the settings.